Following Monday’s multi-national action against the GameOver Zeus botnet, we’re pleased to announce that Microsoft, working closely with the FBI and industry partners, has taken action to remove malware, so that infected computers can no longer be used for harm.
GameOver Zeus, a variant of the Zeus (or Zbot) family of malware, is a highly prevalent password-stealing trojan, according to research by the Microsoft Security Intelligence Report. Dell SecureWorks Counter Threat Unit reports that it was the most active banking trojan of 2013. However, the impact of GameOver Zeus is not limited to the financial industry – nearly all major business and public sector organizations are impacted. Security researchers estimate that between 500,000 and 1 million computers worldwide are infected, and the FBI estimates that Gameover Zeus is responsible for more than $100 million in losses.
The FBI-led legal action and private-sector-led technical action against GameOver Zeus has taken down a portion of the command-and-control (C&C) infrastructure linked to domains generated by the malware and registered by the cyber-criminals. In this operation, codenamed b157, the FBI seized the registered domains. Microsoft did not file a civil action in this matter, unlike some of its previous actions. Unlike most botnet centralized C&C servers, GameOver Zeus uses peer-to-peer (P2P) technology, making its C&C decentralized, more elusive and more resilient than its predecessors.
Microsoft’s role in this technical action was to conduct analysis on the P2P network and develop a cleaning solution. Also, through an additional feed from Shadow Server, we are able to augment our visibility into the number of impacted IP addresses that feed into Microsoft’s Cyber-Threat Intelligence Program (C-TIP), and work closely with global Computer Emergency Response Teams (CERTs) and Internet service providers (ISPs) to help owners of compromised computers regain control of their systems. Based upon these actions, it is anticipated that the cybercriminals’ business model will be disrupted, and they will be forced to rebuild their criminal infrastructure. More importantly, victims of GameOver Zeus have been, and will continue to be, notified and their infected computers cleaned to prevent future harm.
This is the second botnet operation by Microsoft since the Nov. 14 unveiling of the new Microsoft Cybercrime Center – a center of excellence for advancing the global fight against cybercrime – and marks Microsoft’s ninth involvement in a botnet operation. Similar to Microsoft’s December 2013 ZeroAccess botnet case, GameOver Zeus is part of a cooperative effort with industry partners and law enforcement to take out cybercriminal networks to ensure that people worldwide can use their computing devices and services with confidence.
About GameOver Zeus
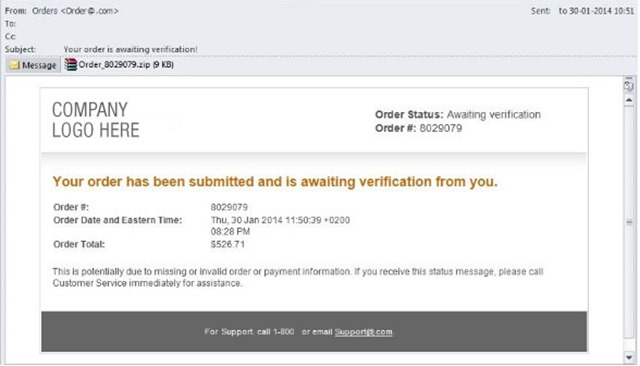
GameOver Zeus is spread through drive-by downloads, where the cybercriminals create a website that downloads malware onto any unprotected computer that visits that site. It is also distributed through the Cutwail spam botnet via phishing, where cybercriminals send counterfeit emails that appear to be legitimate communications from well-known businesses and organizations. These deceptive emails contain realistic language that could entice the recipient to click on a link or attachment, which ultimately deploys the GameOver Zeus malware onto the victim’s computer. The botnet automatically begins key logging when a user of an infected computer types into the Web browser, unwittingly giving cybercriminals access to passwords and private account information. The infected computer sends stolen data to the botnet’s C&C server, and stores it there for later use by the criminal.
GameOver Zeus has many similar properties to Zeus, such as logging keystrokes to steal banking credentials, but it also comes packaged with malicious functions that allow it to launch distributed denial-of-service (DDoS) attacks against financial institutions. Variants have allowed GameOver Zeus to circumvent perimeter security including firewalls, webfilters and network intrusion detection systems, by disguising itself as an encrypted .EXE file. GameOver Zeus also deploys a process known as “web injects,” which provide the ability to modify the HTML of a target website, and inject additional form fields to dupe a victim into entering sensitive information beyond standard banking credentials. In addition to targeting financial institutions, GameOver Zeus has deployed web injects targeting department stores, social networking sites and webmail services. Most recently, a variant is targeting job seekers and recruiters by attempting to steal log-in credentials for popular job search sites. Unlike some of the earlier versions of Zeus, such as ICE IX, Spy Eye and Citadel, GameOver Zeus has not been marketed and offered for sale in the public domain.
This case and operation are ongoing, and we will continue to provide updates as they become available. To stay up to date on the latest developments on the fight against cybercrime, follow the Microsoft Digital Crimes Unit on Facebook and Twitter.
Visit http://support.microsoft.com/gp/cu_sc_virsec_master for detailed instructions on how to remove the GameOver Zeus trojan using malware removal or anti-virus software as quickly as possible.